You cannot build a great building on a weak foundation — and the same principle can be applied to smart factories and their security. Here, Reinhard Mayr, Head of Information Security and Research at automation software supplier COPA-DATA, explains why building a secure architecture in your plant is key for securing digital processes.
Plant infrastructures are becoming increasingly connected, which is driving interconnection.
As a result, plant assets are at a higher risk of attack from external sources and protecting the most important assets should be a priority. However, true plant protection can only be achieved if the entire infrastructure is secure — securing singular assets is not enough.
The harder it is for intruders to reach its target through an infrastructure applying a zoning concept, the less likely they are to overcome these hurdles. In turn, the plant is more secure.
Delicate, digital defence
As a first step to protecting a plant asset, it is essential that plant managers understand what devices need protecting. A good consideration to make is which assets hold the most valuable data and what would have the highest consequences if they were compromised. Once identified, it would be a wise decision to hide the assets behind various defences. This is best achieved by realizing a zoning concept and a defence in depth (DiD) strategy.
A DiD is an information security approach in which a series of security mechanisms and controls are layered through a computer network. This method is used to protect the confidentiality, integrity and availability of the network and the data within.
For instance, external attackers attempting to access plant assets should be met by various layers of technology, acting as hurdles. Using this methodology, if a credential or secret is lost through an asset being breached, these hurdles will not enable the attacker to gain access to other layers in the infrastructure.
Industrial plant deficiencies
There are a plethora of security risks that industrial plants are vulnerable too. We have become accustomed to in the IT world — and even our private lives when managing our personal data. In industry, systems can come under denial-of-service attacks, experience data encryption and even the compromise of operational technology (OT) systems that are reused for the next attack.
However, there is even higher risk for industry in the disguised form of manipulation. For example, a hacker recently initiated an OT cybersecurity attack on an Oldsmar, Florida water treatment facility, which adjusted the levels of sodium hydroxide from 100 parts per million to 11,100 parts per million. At the time, the facility allowed remote access into its ICS systems with a software package called TeamViewer, which was not securely configured and might not have even been authorized with software.
Now picture this. A machine’s settings or batch recipes are slightly adjusted, meaning the plant manager will experience unprecedented quality loss or downtime. At this point — because there is no major or obvious disruption to the plant’s operation — it is hard for the plant manager to know why this is happening. However, the plant has experienced data loss of some kind, which could lead to more damaging financial consequences further down the line.
Despite leaving operators scratching their heads, these scenarios could be prevented through specification standards.
Picking between the standards
Adhering to industrial standards for security can protect plant managers from unexpected risks. Standards like IEC 62443, help create mechanisms by which the policies are enacted to avoid risks — helping plant managers identify threats and act in the event of an attack.
By adhering to a standard, plant owners how to approach a situation and understand the best methods to base their architecture security strategy on. National Institute for Standards and Technology (NIST) and IEC 62443 standards are both good examples of essential standards for an industrial plant.
Generally, NIST Guidelines are much more technical and information technology (IT) driven, despite involving some inputs for operational technology (OT). However, the IEC 62443 standard has more a generic approach and is perfectly suited for plant settings, with a focus on OT. This standard specifies the process requirements for the secure development of products used in industrial automation and control systems, addressing the issue of security for industrial automation and control systems (IACS).
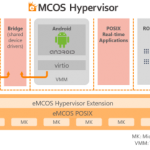
The biggest advantage of IEC 62443 standard is that it defines security requirements for three major players when discussing an OT project; the asset owner, system integrator and a component supplier. In fact, as COPA-DATA’s Secure Development Lifecycle accords to IEC 62443-4-1, its zenon software offers features that can ensure communication across an entire plant’s architecture. Its features are developed to highlight a networks vulnerability and allow security managers to take appropriate action before an intruder reaches its target.
While operators cannot build a fully functioning smart factory on a weak foundation, adhering to specific standards and using the sufficient industrial software ensures a plant’s architecture sets the foundation for secure digital processes.